Performant
Information
Security
Management
System
Performant
Information
Security
Management
System
Performant
Information
Security
Management
System
During our successful ISO 27001 certification in August 2020, many processes could be supported with ecos’ own products. The entire ecos concept is geared towards electronically supporting internal processes, managing equipment, and securing access to rooms and buildings.
ecos – electronically controlled organization systems
Your sensitive business information can be protected with our electronic locker system. Visitors must hand in their mobile devices or USB sticks in an assigned compartment before entering your company’s premises. This protects you from information theft through unauthorized photos or via USB. In addition, information security is increased by making it impossible to introduce malware. This measure can additionally be required for employees without sufficient security clearance.
Both in electronic key cabinet and in electronic locker system, you can use RFID labels and ID recognition to identify their values beyond doubt and log their whereabouts. Even stored items can be recognized and counted in a compartment system with weight recognition.
At any time you can have an overview of your values and can take an inventory list with classification in webman2.

In our webman2 software, you can implement the defined access restrictions per classification level via person or group authorizations. In addition, you can easily check afterward via an overview which recipient has been assigned which values.
All types of data media, such as backups, hard drives, or USB sticks can be stored in our ecos drawer and ecos depots in a controlled manner. Access to highly sensitive information can also be controlled via multifactor/user authentication.
Access to the defined security perimeters required in A 11.1.2 can be ensured and controlled via our terminals. In the process, login and logout of both authorized persons and visitors are logged and controlled. Visitors must provide their email addresses for identification and follow your company’s sign-in process. This may include signing a confidentiality agreement, watching a security video, receiving a visitor badge, or handing over their personal belongings.
Room keys can be managed in our electronic key cabinet and thus each removal and return can be logged with the associated person. Due to the special protection requirements of archive and server rooms, these keys can also be managed in separate small ecos drawer m/4.

The requirement that employees are only informed of the existence of a security area when necessary is also covered by the ecos products. On the system, users can only view what has been released for them according to the “need to know” principle.
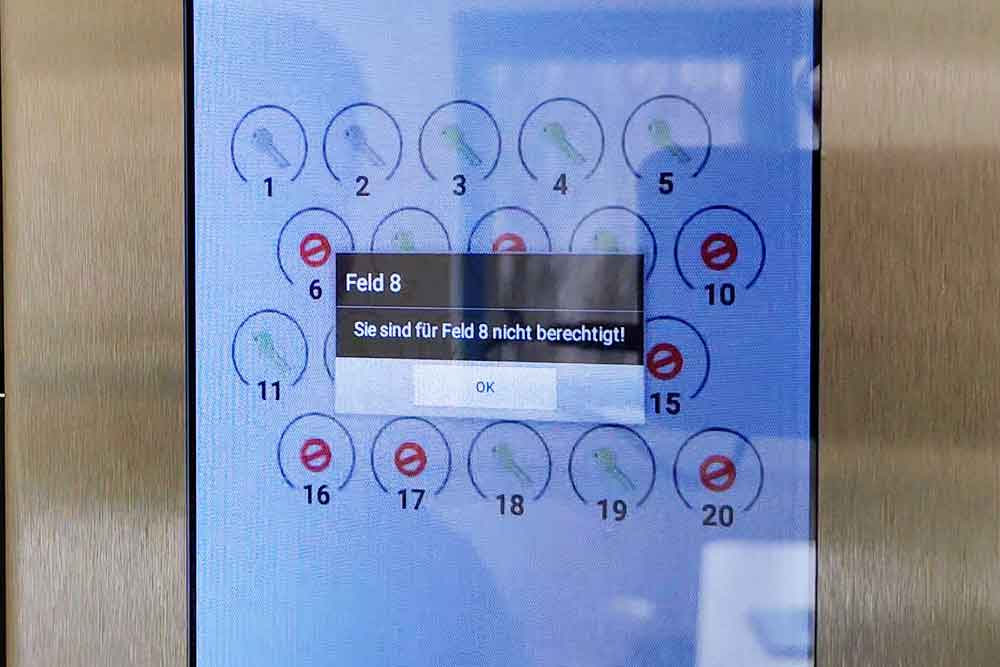
The simple monitoring and protection of access points such as delivery and loading areas can be carried out via our compact terminals. These only allow access to identified and authorized persons.

Our electronic key cabinet and electronic locker system help protect equipment and resources by preventing unauthorized access and reducing the risk of potential threats such as theft or vandalism.


"*" indicates required fields