ecos webman
Web application without software installation
The ecos webman is accessed directly in the Internet browser. The installation of additional software is therefore not necessary. Updates and new features, which ecos systems introduces on a regular basis, are available immediately at no additional cost – so there is no need for updates on the customer’s side. The ecos webman can be used with any Internet-capable device, similar to online banking.
Local installation always possible
Of course, you can still have ecos webman and all modules such as ecos reserve and ecos alarm as a local installation on your server. Our technicians will be happy to accompany you during the installation.
Real-time status & actions
In the software you can see the status of your ecos system in real time. 14 different statuses always show you how your keys and objects are doing. If an employee accidentally forgets their access medium or exceptionally needs a spontaneous authorisation, actions can be carried out on the electronic key cabinet or the locker system by remote release in real time. Of course, updates to the rights are also transmitted immediately.
In the software you can see the status of your ecos system in real time. 14 different statuses always show you how your keys and objects are doing. If an employee accidentally forgets his access medium or exceptionally needs a spontaneous authorisation, actions can be carried out on the electronic key cabinet or the locker system by remote release in real time. Of course, updates to the rights are also transmitted immediately.
Intelligent rights concept – for user and object groups
Access rights must be assigned with care. However, this can quickly become confusing with individual access rights per user or object. The potential for security-critical errors is too high. For this reason, ecos webman offers the possibility of defining user groups and object groups.
In the case of users, the who, there are usually similar logical structures, such as caretakers, truck drivers, employees from building 2 or even half-day employees. All corresponding persons are then assigned to these groups. For objects, the what, this logical grouping is set up in the same way. Examples are: Electric pool car keys, entrance door keys, long guns, sales smartphones. The corresponding keys or objects are then assigned to these groups.
In the final step, the corresponding object groups are assigned to the user groups. As a result, the creation and maintenance of rights is very simple. When an object is removed from its object group, the rights update immediately for all, sometimes thousands, of users.
Of course, a user can also have individual object rights in parallel, e.g. his locker.
Access rights must be assigned with care. However, this can quickly become confusing with individual access rights per user or object. The potential for security-critical errors is too high. For this reason, ecos webman offers the possibility of defining user groups and object groups.
In the case of users, the who, there are usually similar logical structures, such as caretakers, truck drivers, employees from building 2 or even half-day employees. All corresponding persons are then assigned to these groups. For objects, the what, this logical grouping is set up in the same way. Examples are: Electric pool car keys, entrance door keys, long guns, sales smartphones. The corresponding keys or objects are then assigned to these groups.
In the final step, the corresponding object groups are assigned to the user groups. As a result, the creation and maintenance of rights is very simple. When an object is removed from its object group, the rights update immediately for all, sometimes thousands, of users.
Of course, a user can also have individual object rights in parallel, e.g. his locker.
If several systems are to be managed at different locations, they can be bundled into one system group. In this way, keys & objects can be moved across locations from one cabinet or locker system to the next. At any time, the location is traceable in the software.
In order to further adapt the assignment of rights to your company, access times can be set for users, objects and the respective groups. Here, you can then set exactly when the specific user has access to rooms/buildings, key cabinets or specialist facilities. In addition, it can be set on which days and at which times certain objects can be removed by users.
These then add up.
37 different actions are tracked in our software. These are displayed in chronological order and with various filter functions a precise understanding of the use of your system can be obtained.
A dozen of the most common reports can be downloaded from ecos webman ad-hoc or sent to you periodically.
There are 6 predefined roles with varying levels of authorisation in ecos webman and in the ecos app. These range from simple report readers to superadmin. The roles have a granular determination of rights, which not only allows access to certain functions, but also the determination of the degree to which the function can be used in detail. You can easily create your own defined roles and check and uncheck in the software which rights are to be assigned and how.
The ecos app – the mobile assistant
Times are changing, nowadays apps are on everyone’s lips and are used daily in one form or another. Why then not also for the management of keys, objects and accesses in your company? For this reason, the ecos app can do almost everything that the ecos webman can. Here is a selection of the most important functions:





This is how our systems are used!
Most of our customers use our 7″ control unit to interact with the key cabinet, locker system or terminal. All functions of the ecos webman can also be done in stand-alone mode on the system. Accordingly, there are many screen displays that can be used.
To give you a better understanding of what you and your organisation will end up using, we show you the most commonly used interfaces here.






Our modules
ecos alarm
The included functionalities help especially in an environment with high security standards. With 21 predefined alarm types and adjustable transmission routines, your systems are holistically protected. This module is included free of charge in ecos care.
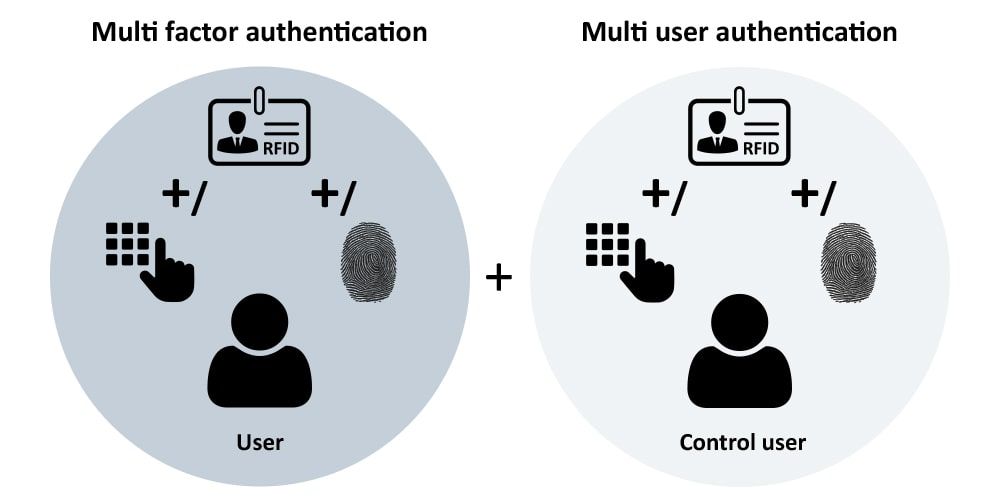
Multi authentication
For particularly large companies and security-critical applications, our “Alarm” module offers multi-authentication. This makes it possible to create individual identification routines and processes. In addition to the combination of one or more PIN codes, RFID cards and biometric features, the user’s identity can also be confirmed by one or more other persons. Additional security can be enabled by a TAN procedure. By default, you can set the expiry date of the access as well as hourly access times.
Immediate notification
In addition to the physical alarms, there is also a wide range of digital alarm options. Since things usually have to happen quickly, these can be displayed on all kinds of devices, just like our software. Besides the notifications via the web software, a push notification is sent via the ecos app. In addition, an email can also be sent.
Potential-free contacts
The 4 potential-free contacts can be configured via the ecos Webman. Here, actions can be triggered directly for the most time-critical as well as most important triggers, which are not only displayed in the software. The potential-free contacts can, for example, directly lock the door of the room or forward it to the internal control centre, but also alert the police authorities. More than 20 alarm triggers complete the spectrum of possible reactions to security risks. The most important ones are when the key cabinet has been taken down, an object in the locker is removed without the door open or the return time is exceeded.

Alarm configuration
With this function, you can set the routines and the responsible persons or groups. For each alarm, you can decide to whom it should go, how it should be sent and who can defuse and control the alarm.

Alarm overview
A chronological list of all alarms that have ever been triggered. This makes it possible to see to whom the alarm was forwarded and whether this alarm was resolved. If a responsible person is available, actions can be taken and rights changed.
This software module makes it possible to make reservations for keys and objects. Each user can make reservations for himself or, if authorised, for other internal employees. In addition, guest reservations can be made for external third parties (e.g. service providers or visitors). For maximum user-friendliness, all functions can be used via the ecos app and reservations can also be booked via Outlook.
The reservation functions have been further adapted to vehicles in the ecos fleet module. Among other things, ecos fleet contains more damage reports or maintenance reservations.
With small numbers of keys or objects to be managed, it is usually easier to reserve the specific ones needed. Simultaneous requests for use become clear days in advance and can be clarified. No hectic organising at the moment it is needed.
With a larger number of rooms, laptops or vehicles, it becomes increasingly difficult to organise them with 1 to 1 reservations. Manual clarifications are hardly possible. Accordingly, logical categories such as rooms of the same size or the same vehicle classes are assigned to an object group. This enables a group reservation in which any object with the right characteristics is reserved. The user does not have to choose one.
For outpatient care services, monitoring routes or jour-fixe meetings, objects can be reserved in a recurring manner. This means that the same reservation does not have to be made every week.
The ecos webman and software modules offer freely definable fields throughout. You can customise these to suit your company.
ecos reserve
This software module makes it possible to make reservations for keys and objects. Each user can make reservations for himself or, if authorised, for other internal employees. In addition, guest reservations can be made for external third parties (e.g. service providers or visitors). For maximum user-friendliness, all functions can be used via the ecos app and reservations can also be booked via Outlook.
The reservation functions have been further adapted to vehicles in the ecos fleet module. Among other things, ecos fleet contains more damage reports or maintenance reservations.
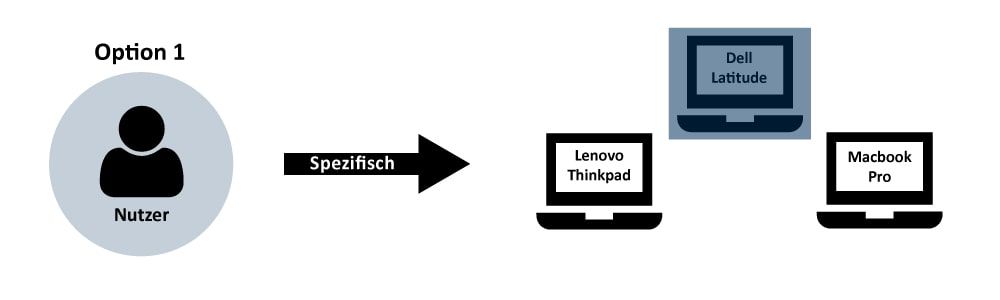
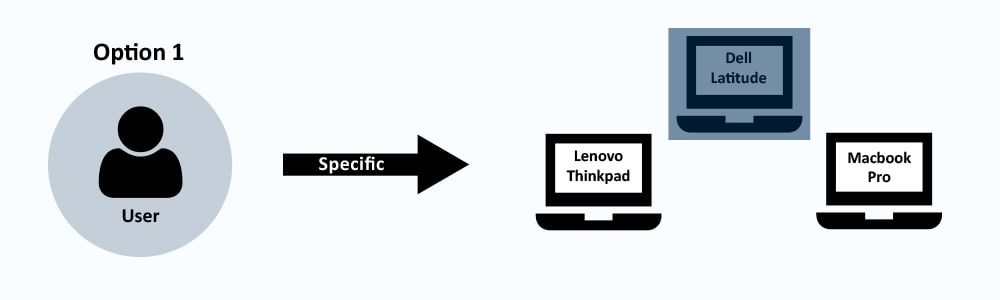
Specific Reservation (1 to 1)
With small numbers of keys or objects to be managed, it is usually easier to reserve the specific ones needed. Simultaneous requests for use become clear days in advance and can be clarified. No hectic organising at the moment it is needed.
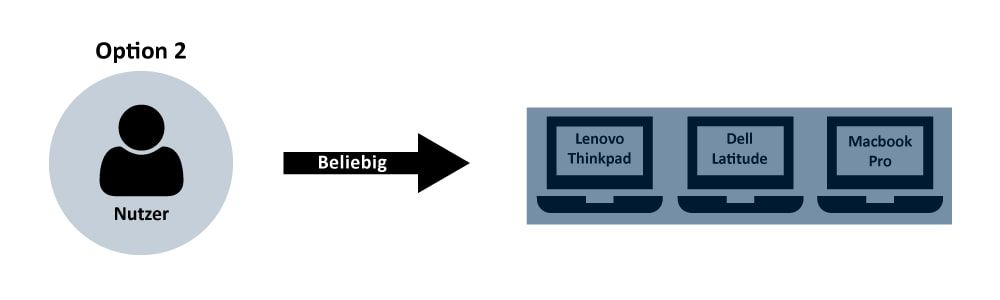
Group reservation (1 to n)
With a larger number of rooms, laptops or vehicles, it becomes increasingly difficult to organise them with 1 to 1 reservations. Manual clarifications are hardly possible. Accordingly, logical categories such as rooms of the same size or the same vehicle classes are assigned to an object group. This enables a group reservation in which any object with the right characteristics is reserved. The user does not have to choose one.
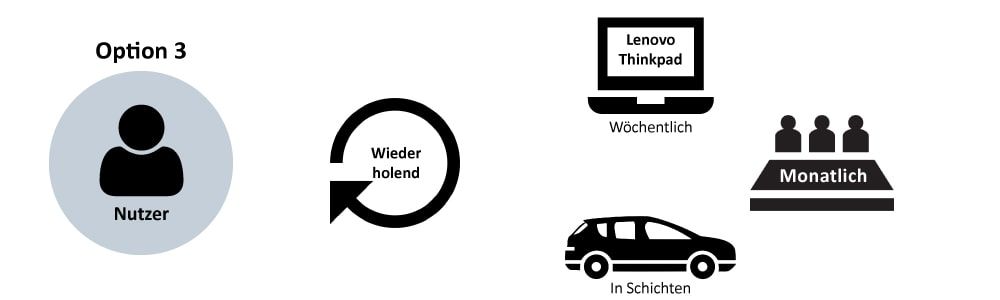
Recurring reservation
For outpatient care services, monitoring routes or jour-fixe meetings, objects can be reserved in a recurring manner. This means that the same reservation does not have to be made every week.
Customisable fields
The ecos webman and software modules offer freely definable fields throughout. You can customise these to suit your company.
ecos time
ecos time enables your employees to reliably log in and out of the system directly at the beginning and end of work. The individual log times are listed in detail in our overview.
-

Users log in and out of their work mostly using the terminal. Identification is carried out using the familiar methods (PIN code, RFID card or biometrics). The subsequent actions require only one click. In addition, the terminal can be used to control the first entrance door via potential-free contacts.
-
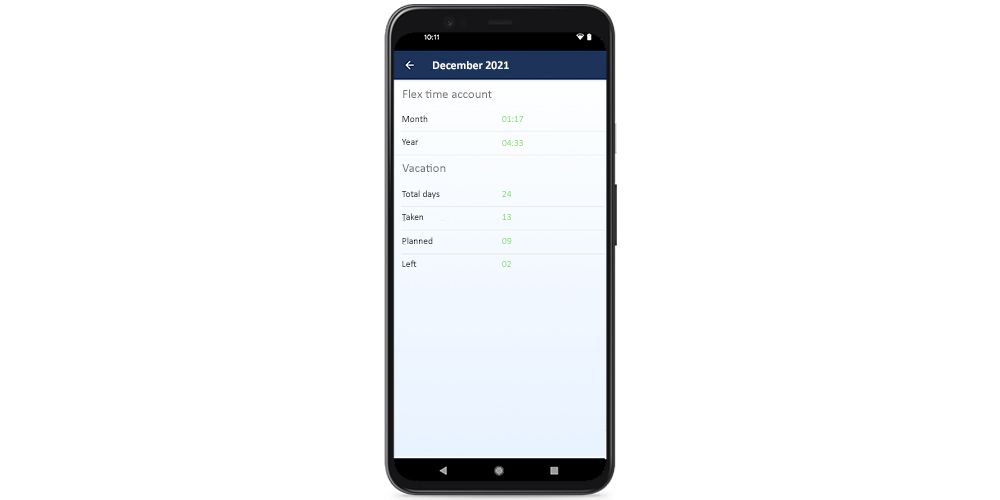
The administration of sick days and holiday requests, as well as the analysis of clocking-in times in an hourly account per employee are available in this module. Your company can use this to digitise requests and confirmations and secure them with a physical access terminal.
In addition to public holidays and company-wide holidays, several individual work schedules can be created in the settings and then applied to different user groups (departments). Individual working hours and goodwill time settings can also be configured.
-
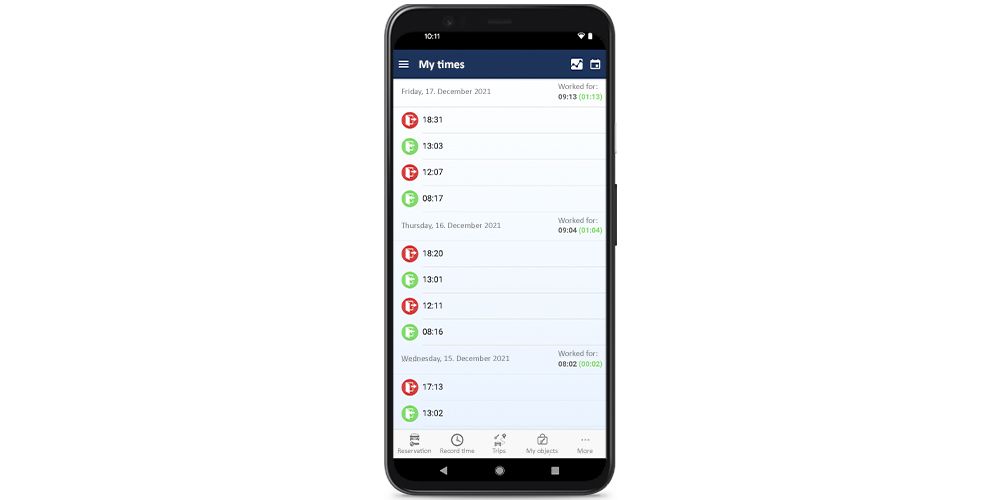
Uniform software is indispensable for the cost-saving and simple implementation of time management. For this reason, the time module includes a user app that allows your employees to log in and out as soon as they are working from home or on the road.
Easy data exchange with the help of the ecos API

There are now numerous digital applications for the efficient management of different departments in your company (e.g. access control or control centre). A bundling of different solutions in one platform is essential to avoid an overflow of apps and applications. Individual “island solutions” require significant additional effort for data maintenance and, moreover, this can lead to errors.
Numerous functions can be integrated into other systems and apps via the ecos API. The ecos API is based on the SOAP/REST protocol. Any software developer can use simple HTTPS access via the Internet to integrate the functions into their own software. We are happy to advise developers and offer support should adaptations be necessary for the specific use case.
As an alternative to bidirectional fully automated control, we also offer data import via intermediate files such as CSV or data exchange via directory services such as LDAP.
It doesn’t get any safer than this. Officially tested and audited.

End-to-end encrypted information
We use the most modern security measures. All ecos app or ecos webman data is transferred securely using TLS v1.2. Data at Rest is encrypted using AES256. Internal communication in the systems, between the main processor and the microprocessors on the CAN bus, is secured using elliptical asymmetric encryption ECC with 233 bits.

Tested stability
Our software has passed penetration tests by independent test institutes. This is why two major European military organisations use our web-based software.

IT infrastructure in line with the highest standards
Our entire IT infrastructure is certified, right up to the TIER IV data centre. We comply with all EU directives and laws and are constantly adapting to new requirements and laws in various countries in order to offer the highest possible security.

Stand-alone – Administration only on the system
In the case of a very high security requirement, our products can function and be configured completely locally. This ensures that no external communication is possible. With its own database and an internal SD card for backups, data integrity is ensured even in the event of a processor failure.

Audited by external auditors
To meet the highest standards, we have ourselves audited four times a year by external auditing bodies. These ensure that our specifications are met and that our safety promise to you is maintained and continuously improved.

Integrated data protection
With an in-house data protection expert, we ensure that your customer data is handled in compliance with the GDPR at all times. With built-in software functions, we automatically support you in working in a data protection-compliant manner.